Documentation
¶
Documentation
¶
Index ¶
- Constants
- Variables
- func LoadCertificate(certFile, keyFile string) (tls.Certificate, error)
- func SetDefaultCertificate(rawCert, rawKey []byte)
- func ToSocksAddr(addr net.Addr) *gosocks5.Addr
- type Http2Server
- type HttpServer
- type KCPConfig
- type KCPConn
- func (c *KCPConn) Close() error
- func (c *KCPConn) LocalAddr() net.Addr
- func (c *KCPConn) Read(b []byte) (n int, err error)
- func (c *KCPConn) RemoteAddr() net.Addr
- func (c *KCPConn) SetDeadline(t time.Time) error
- func (c *KCPConn) SetReadDeadline(t time.Time) error
- func (c *KCPConn) SetWriteDeadline(t time.Time) error
- func (c *KCPConn) Write(b []byte) (n int, err error)
- type KCPServer
- type KCPSession
- type ProxyChain
- func (c *ProxyChain) AddProxyNode(node ...ProxyNode)
- func (c *ProxyChain) AddProxyNodeString(snode ...string) error
- func (c *ProxyChain) Dial(addr string) (net.Conn, error)
- func (c *ProxyChain) GetConn() (net.Conn, error)
- func (c *ProxyChain) GetNode(index int) *ProxyNode
- func (c *ProxyChain) Http2Enabled() bool
- func (c *ProxyChain) Init()
- func (c *ProxyChain) KCPEnabled() bool
- func (c *ProxyChain) Nodes() []ProxyNode
- func (c *ProxyChain) SetNode(index int, node ProxyNode)
- type ProxyConn
- func (c *ProxyConn) Close() error
- func (c *ProxyConn) Connect(addr string) error
- func (c *ProxyConn) Handshake() error
- func (c *ProxyConn) LocalAddr() net.Addr
- func (c *ProxyConn) Read(b []byte) (n int, err error)
- func (c *ProxyConn) RemoteAddr() net.Addr
- func (c *ProxyConn) SetDeadline(t time.Time) error
- func (c *ProxyConn) SetReadDeadline(t time.Time) error
- func (c *ProxyConn) SetWriteDeadline(t time.Time) error
- func (c *ProxyConn) Write(b []byte) (n int, err error)
- type ProxyNode
- type ProxyServer
- type QuicServer
- type RTcpForwardServer
- type RUdpForwardServer
- type RedsocksTCPServer
- type ShadowServer
- type ShadowUdpServer
- type Socks5Server
- type TcpForwardServer
- type UdpForwardServer
- type WebsocketConn
- func (c *WebsocketConn) Close() error
- func (c *WebsocketConn) LocalAddr() net.Addr
- func (c *WebsocketConn) Read(b []byte) (n int, err error)
- func (c *WebsocketConn) RemoteAddr() net.Addr
- func (conn *WebsocketConn) SetDeadline(t time.Time) error
- func (c *WebsocketConn) SetReadDeadline(t time.Time) error
- func (c *WebsocketConn) SetWriteDeadline(t time.Time) error
- func (c *WebsocketConn) Write(b []byte) (n int, err error)
- type WebsocketServer
Constants ¶
const ( LFATAL = iota LERROR LWARNING LINFO LDEBUG )
Log level for glog
const ( MethodTLS uint8 = 0x80 // extended method for tls MethodTLSAuth uint8 = 0x82 // extended method for tls+auth )
const (
CmdUdpTun uint8 = 0xF3 // extended method for udp over tcp
)
const (
DefaultKCPConfigFile = "kcp.json"
)
const (
SO_ORIGINAL_DST = 80
)
const (
Version = "2.4-dev"
)
Variables ¶
var ( KeepAliveTime = 180 * time.Second DialTimeout = 30 * time.Second ReadTimeout = 90 * time.Second WriteTimeout = 90 * time.Second DefaultTTL = 60 // default udp node TTL in second for udp port forwarding )
var ( SmallBufferSize = 1 * 1024 // 1KB small buffer MediumBufferSize = 8 * 1024 // 8KB medium buffer LargeBufferSize = 32 * 1024 // 32KB large buffer )
var ( DefaultCertFile = "cert.pem" DefaultKeyFile = "key.pem" )
var ( DefaultKCPConfig = &KCPConfig{ Key: "it's a secrect", Crypt: "aes", Mode: "fast", MTU: 1350, SndWnd: 1024, RcvWnd: 1024, DataShard: 10, ParityShard: 3, DSCP: 0, NoComp: false, AckNodelay: false, NoDelay: 0, Interval: 40, Resend: 0, NoCongestion: 0, SockBuf: 4194304, KeepAlive: 10, } )
var (
ErrEmptyChain = errors.New("empty chain")
)
var (
SALT = "kcp-go"
)
Functions ¶
func LoadCertificate ¶
func LoadCertificate(certFile, keyFile string) (tls.Certificate, error)
Load the certificate from cert and key files, will use the default certificate if the provided info are invalid.
func SetDefaultCertificate ¶
func SetDefaultCertificate(rawCert, rawKey []byte)
Replace the default certificate by your own
Types ¶
type Http2Server ¶
type Http2Server struct {
Base *ProxyServer
Handler http.Handler
TLSConfig *tls.Config
}
func NewHttp2Server ¶
func NewHttp2Server(base *ProxyServer) *Http2Server
func (*Http2Server) HandleRequest ¶
func (s *Http2Server) HandleRequest(w http.ResponseWriter, req *http.Request)
Default HTTP2 server handler
func (*Http2Server) ListenAndServeTLS ¶
func (s *Http2Server) ListenAndServeTLS(config *tls.Config) error
func (*Http2Server) Upgrade ¶
func (s *Http2Server) Upgrade(w http.ResponseWriter, r *http.Request) (net.Conn, error)
Upgrade upgrade an HTTP2 request to a bidirectional connection that preparing for tunneling other protocol, just like a websocket connection.
type HttpServer ¶
type HttpServer struct {
Base *ProxyServer
// contains filtered or unexported fields
}
func NewHttpServer ¶
func NewHttpServer(conn net.Conn, base *ProxyServer) *HttpServer
func (*HttpServer) HandleRequest ¶
func (s *HttpServer) HandleRequest(req *http.Request)
Default HTTP server handler
type KCPConfig ¶
type KCPConfig struct {
Key string `json:"key"`
Crypt string `json:"crypt"`
Mode string `json:"mode"`
MTU int `json:"mtu"`
SndWnd int `json:"sndwnd"`
RcvWnd int `json:"rcvwnd"`
DataShard int `json:"datashard"`
ParityShard int `json:"parityshard"`
DSCP int `json:"dscp"`
NoComp bool `json:"nocomp"`
AckNodelay bool `json:"acknodelay"`
NoDelay int `json:"nodelay"`
Interval int `json:"interval"`
Resend int `json:"resend"`
NoCongestion int `json:"nc"`
SockBuf int `json:"sockbuf"`
KeepAlive int `json:"keepalive"`
}
func ParseKCPConfig ¶
type KCPConn ¶
type KCPConn struct {
// contains filtered or unexported fields
}
func NewKCPConn ¶
func (*KCPConn) RemoteAddr ¶
type KCPServer ¶
type KCPServer struct {
Base *ProxyServer
Config *KCPConfig
}
func NewKCPServer ¶
func NewKCPServer(base *ProxyServer, config *KCPConfig) *KCPServer
func (*KCPServer) ListenAndServe ¶
type KCPSession ¶
type KCPSession struct {
// contains filtered or unexported fields
}
func (*KCPSession) Close ¶
func (session *KCPSession) Close() error
func (*KCPSession) GetConn ¶
func (session *KCPSession) GetConn() (*KCPConn, error)
func (*KCPSession) IsClosed ¶
func (session *KCPSession) IsClosed() bool
func (*KCPSession) NumStreams ¶
func (session *KCPSession) NumStreams() int
type ProxyChain ¶
type ProxyChain struct {
// contains filtered or unexported fields
}
Proxy chain holds a list of proxy nodes
func NewProxyChain ¶
func NewProxyChain(nodes ...ProxyNode) *ProxyChain
func (*ProxyChain) AddProxyNode ¶
func (c *ProxyChain) AddProxyNode(node ...ProxyNode)
func (*ProxyChain) AddProxyNodeString ¶
func (c *ProxyChain) AddProxyNodeString(snode ...string) error
func (*ProxyChain) Dial ¶
func (c *ProxyChain) Dial(addr string) (net.Conn, error)
Connect to addr through proxy chain
func (*ProxyChain) GetConn ¶
func (c *ProxyChain) GetConn() (net.Conn, error)
GetConn initializes a proxy chain connection, if no proxy nodes on this chain, it will return error
func (*ProxyChain) GetNode ¶
func (c *ProxyChain) GetNode(index int) *ProxyNode
func (*ProxyChain) Http2Enabled ¶
func (c *ProxyChain) Http2Enabled() bool
func (*ProxyChain) Init ¶
func (c *ProxyChain) Init()
Init initialize the proxy chain. KCP will be enabled if the first proxy node is KCP proxy (transport == kcp). HTTP2 will be enabled when at least one HTTP2 proxy node (scheme == http2) is present.
NOTE: Should be called immediately when proxy nodes are ready.
func (*ProxyChain) KCPEnabled ¶
func (c *ProxyChain) KCPEnabled() bool
func (*ProxyChain) Nodes ¶
func (c *ProxyChain) Nodes() []ProxyNode
func (*ProxyChain) SetNode ¶
func (c *ProxyChain) SetNode(index int, node ProxyNode)
type ProxyConn ¶
type ProxyConn struct {
Node ProxyNode
// contains filtered or unexported fields
}
func (*ProxyConn) Handshake ¶
Handshake handshake with this proxy node based on the proxy node info: transport, protocol, authentication, etc.
NOTE: any HTTP2 scheme will be treated as http (for protocol) or tls (for transport).
func (*ProxyConn) RemoteAddr ¶
type ProxyNode ¶
type ProxyNode struct {
Addr string // [host]:port
Protocol string // protocol: http/socks5/ss
Transport string // transport: ws/wss/tls/http2/tcp/udp/rtcp/rudp
Remote string // remote address, used by tcp/udp port forwarding
Users []*url.Userinfo // authentication for proxy
// contains filtered or unexported fields
}
Proxy node represent a proxy
func ParseProxyNode ¶
The proxy node string pattern is [scheme://][user:pass@host]:port.
Scheme can be devided into two parts by character '+', such as: http+tls.
type ProxyServer ¶
type ProxyServer struct {
Node ProxyNode
Chain *ProxyChain
TLSConfig *tls.Config
// contains filtered or unexported fields
}
func NewProxyServer ¶
func NewProxyServer(node ProxyNode, chain *ProxyChain, config *tls.Config) *ProxyServer
func (*ProxyServer) Serve ¶
func (s *ProxyServer) Serve() error
type QuicServer ¶
type QuicServer struct {
Base *ProxyServer
Handler http.Handler
TLSConfig *tls.Config
}
func NewQuicServer ¶
func NewQuicServer(base *ProxyServer) *QuicServer
func (*QuicServer) HandleRequest ¶
func (s *QuicServer) HandleRequest(w http.ResponseWriter, req *http.Request)
func (*QuicServer) ListenAndServeTLS ¶
func (s *QuicServer) ListenAndServeTLS(config *tls.Config) error
type RTcpForwardServer ¶
type RTcpForwardServer struct {
Base *ProxyServer
}
func NewRTcpForwardServer ¶
func NewRTcpForwardServer(base *ProxyServer) *RTcpForwardServer
func (*RTcpForwardServer) Serve ¶
func (s *RTcpForwardServer) Serve() error
type RUdpForwardServer ¶
type RUdpForwardServer struct {
Base *ProxyServer
}
func NewRUdpForwardServer ¶
func NewRUdpForwardServer(base *ProxyServer) *RUdpForwardServer
func (*RUdpForwardServer) Serve ¶
func (s *RUdpForwardServer) Serve() error
type RedsocksTCPServer ¶
type RedsocksTCPServer struct {
Base *ProxyServer
}
func NewRedsocksTCPServer ¶
func NewRedsocksTCPServer(base *ProxyServer) *RedsocksTCPServer
func (*RedsocksTCPServer) ListenAndServe ¶
func (s *RedsocksTCPServer) ListenAndServe() error
type ShadowServer ¶
type ShadowServer struct {
Base *ProxyServer
OTA bool // one time auth
// contains filtered or unexported fields
}
func NewShadowServer ¶
func NewShadowServer(conn *ss.Conn, base *ProxyServer) *ShadowServer
func (*ShadowServer) Serve ¶
func (s *ShadowServer) Serve()
type ShadowUdpServer ¶
type ShadowUdpServer struct {
Base *ProxyServer
TTL int
}
func NewShadowUdpServer ¶
func NewShadowUdpServer(base *ProxyServer, ttl int) *ShadowUdpServer
func (*ShadowUdpServer) ListenAndServe ¶
func (s *ShadowUdpServer) ListenAndServe() error
type Socks5Server ¶
type Socks5Server struct {
Base *ProxyServer
// contains filtered or unexported fields
}
func NewSocks5Server ¶
func NewSocks5Server(conn net.Conn, base *ProxyServer) *Socks5Server
func (*Socks5Server) HandleRequest ¶
func (s *Socks5Server) HandleRequest(req *gosocks5.Request)
type TcpForwardServer ¶
type TcpForwardServer struct {
Base *ProxyServer
Handler func(conn net.Conn, raddr net.Addr)
}
func NewTcpForwardServer ¶
func NewTcpForwardServer(base *ProxyServer) *TcpForwardServer
func (*TcpForwardServer) ListenAndServe ¶
func (s *TcpForwardServer) ListenAndServe() error
type UdpForwardServer ¶
type UdpForwardServer struct {
Base *ProxyServer
TTL int
}
func NewUdpForwardServer ¶
func NewUdpForwardServer(base *ProxyServer, ttl int) *UdpForwardServer
func (*UdpForwardServer) ListenAndServe ¶
func (s *UdpForwardServer) ListenAndServe() error
type WebsocketConn ¶
type WebsocketConn struct {
// contains filtered or unexported fields
}
func WebsocketClientConn ¶
func WebsocketServerConn ¶
func WebsocketServerConn(conn *websocket.Conn) *WebsocketConn
func (*WebsocketConn) Close ¶
func (c *WebsocketConn) Close() error
func (*WebsocketConn) LocalAddr ¶
func (c *WebsocketConn) LocalAddr() net.Addr
func (*WebsocketConn) RemoteAddr ¶
func (c *WebsocketConn) RemoteAddr() net.Addr
func (*WebsocketConn) SetDeadline ¶
func (conn *WebsocketConn) SetDeadline(t time.Time) error
func (*WebsocketConn) SetReadDeadline ¶
func (c *WebsocketConn) SetReadDeadline(t time.Time) error
func (*WebsocketConn) SetWriteDeadline ¶
func (c *WebsocketConn) SetWriteDeadline(t time.Time) error
type WebsocketServer ¶
type WebsocketServer struct {
Addr string
Base *ProxyServer
Handler http.Handler
// contains filtered or unexported fields
}
func NewWebsocketServer ¶
func NewWebsocketServer(base *ProxyServer) *WebsocketServer
func (*WebsocketServer) HandleRequest ¶
func (s *WebsocketServer) HandleRequest(w http.ResponseWriter, r *http.Request)
Default websocket server handler
func (*WebsocketServer) ListenAndServe ¶
func (s *WebsocketServer) ListenAndServe() error
func (*WebsocketServer) ListenAndServeTLS ¶
func (s *WebsocketServer) ListenAndServeTLS(config *tls.Config) error
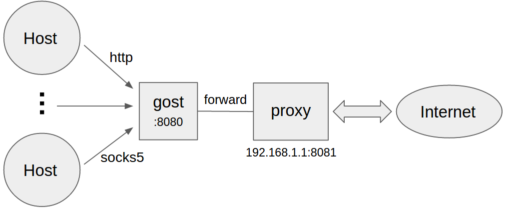 ```bash
gost -L=:8080 -F=192.168.1.1:8081
```
```bash
gost -L=:8080 -F=192.168.1.1:8081
```
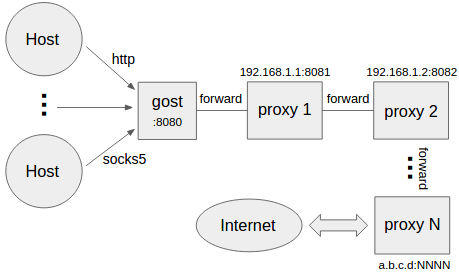 ```bash
gost -L=:8080 -F=http+tls://192.168.1.1:443 -F=socks+ws://192.168.1.2:1080 -F=ss://aes-128-cfb:123456@192.168.1.3:8338 -F=a.b.c.d:NNNN
```
gost按照-F设置的顺序通过代理链将请求最终转发给a.b.c.d:NNNN处理,每一个转发代理可以是任意HTTP/HTTPS/HTTP2/SOCKS5/Shadowsocks类型代理。
```bash
gost -L=:8080 -F=http+tls://192.168.1.1:443 -F=socks+ws://192.168.1.2:1080 -F=ss://aes-128-cfb:123456@192.168.1.3:8338 -F=a.b.c.d:NNNN
```
gost按照-F设置的顺序通过代理链将请求最终转发给a.b.c.d:NNNN处理,每一个转发代理可以是任意HTTP/HTTPS/HTTP2/SOCKS5/Shadowsocks类型代理。