Documentation
¶
Documentation
¶
Index ¶
- Constants
- func Asset(name string) ([]byte, error)
- func AssetDigest(name string) ([sha256.Size]byte, error)
- func AssetDir(name string) ([]string, error)
- func AssetInfo(name string) (os.FileInfo, error)
- func AssetNames() []string
- func AssetString(name string) (string, error)
- func CreateKeychainEntryForService(service, account, password string, trustedApplications []string) error
- func CreateOrUpdateKeychainEntriesForService(service, account, password string, trustedApplications []string) error
- func Digests() (map[string][sha256.Size]byte, error)
- func DynamicUnmarshalYamlAmanarConfiguration(data []byte) (map[interface{}]interface{}, error)
- func HandleResultErrors(resultErrors []gojsonschema.ResultError)
- func MustAsset(name string) []byte
- func MustAssetString(name string) string
- func ProcessAmanar(githubToken string, a *Amanar)
- func ProcessAmanarWithWriter(githubToken string, a *Amanar, writer io.Writer)
- func ProcessConstantConfigItem(constant Constant, writer io.Writer)
- func ProcessVaultConfigItem(configurables *Configurables, credentials *Credentials, writer io.Writer)
- func RestoreAsset(dir, name string) error
- func RestoreAssets(dir, name string) error
- func UpdateCredentials(flows []Flower, credentials *Credentials)
- func ValidateConfiguration(documentLoader gojsonschema.JSONLoader) (err error, re []gojsonschema.ResultError)
- type Amanar
- type AmanarConfiguration
- type Configurables
- type ConfigurationProcessor
- type Constant
- type ConstantConfigurationProcessor
- type Credentials
- type Flower
- type GithubLoginBody
- type IntellijDatasource
- type IntellijDatasourceFile
- type IntellijDatasourceFlow
- type IntellijRunConfig
- type IntellijRunConfigsFlow
- type IntellijRunConfiguration
- type JSONCredential
- type JSONCredentials
- type JSONDatasource
- type JSONFlow
- type JsonBytesSchemaValidator
- type PosticoDatasource
- type PosticoFavorite
- type PosticoFlow
- type PosticoSQLiteDatabase
- type Querious2Datasource
- type Querious2Flow
- type Querious2SQLiteDatabase
- type SchemaValidator
- type SequelProDatasource
- type SequelProFlow
- type SequelProPlistItem
- type SequelProRootPlist
- type ShellDatasource
- type ShellFile
- type ShellFlow
- type StructSchemaValidator
- type TemplateDatasource
- type TemplateDefiner
- type TemplateFlow
- type TemplateSource
- func NewTemplateSource(definer TemplateDefiner, writer io.Writer) (source *TemplateSource, err error)
- func NewTemplateSourceFromFile(templateFilepath *string, writer io.Writer) (*TemplateSource, error)
- func NewTemplateSourceFromString(templateString *string, writer io.Writer) (*TemplateSource, error)
- type VaultConfiguration
- type VaultConfigurationProcessor
- type VaultGithubAuthClient
Constants ¶
const SEQUEL_PRO_PLIST_FORMAT = plist.XMLFormat
Variables ¶
This section is empty.
Functions ¶
func Asset ¶
Asset loads and returns the asset for the given name. It returns an error if the asset could not be found or could not be loaded.
func AssetDigest ¶
AssetDigest returns the digest of the file with the given name. It returns an error if the asset could not be found or the digest could not be loaded.
func AssetDir ¶
AssetDir returns the file names below a certain directory embedded in the file by go-bindata. For example if you run go-bindata on data/... and data contains the following hierarchy:
data/
foo.txt
img/
a.png
b.png
then AssetDir("data") would return []string{"foo.txt", "img"}, AssetDir("data/img") would return []string{"a.png", "b.png"}, AssetDir("foo.txt") and AssetDir("notexist") would return an error, and AssetDir("") will return []string{"data"}.
func AssetInfo ¶
AssetInfo loads and returns the asset info for the given name. It returns an error if the asset could not be found or could not be loaded.
func AssetString ¶
AssetString returns the asset contents as a string (instead of a []byte).
func CreateKeychainEntryForService ¶
func CreateKeychainEntryForService(service, account, password string, trustedApplications []string) error
Creates a new keychain entry and
func CreateOrUpdateKeychainEntriesForService ¶
func CreateOrUpdateKeychainEntriesForService(service, account, password string, trustedApplications []string) error
Deletion poses problems because there does not seem to be a way to make deletion prompt for access, which means it will fail. trustedApplications is only set when creating a new keychain entry. Q: what happens when updating?
func HandleResultErrors ¶
func HandleResultErrors(resultErrors []gojsonschema.ResultError)
func MustAsset ¶
MustAsset is like Asset but panics when Asset would return an error. It simplifies safe initialization of global variables.
func MustAssetString ¶
MustAssetString is like AssetString but panics when Asset would return an error. It simplifies safe initialization of global variables.
func ProcessAmanar ¶
This is the main entrypoint for Amanar. Given a Github Token and a valid Amanar configuration, performs the necessary side effects.
func ProcessAmanarWithWriter ¶
func ProcessVaultConfigItem ¶
func ProcessVaultConfigItem(configurables *Configurables, credentials *Credentials, writer io.Writer)
func RestoreAsset ¶
RestoreAsset restores an asset under the given directory.
func RestoreAssets ¶
RestoreAssets restores an asset under the given directory recursively.
func UpdateCredentials ¶
func UpdateCredentials(flows []Flower, credentials *Credentials)
func ValidateConfiguration ¶
func ValidateConfiguration(documentLoader gojsonschema.JSONLoader) (err error, re []gojsonschema.ResultError)
Types ¶
type Amanar ¶
type Amanar struct {
AmanarConfiguration []AmanarConfiguration `json:"amanar_configuration" yaml:"amanar_configuration"`
}
func LoadConfiguration ¶
func LoadConfiguration(configFilepath string) (*Amanar, error, []gojsonschema.ResultError)
func UnmarshalAmanar ¶
type AmanarConfiguration ¶
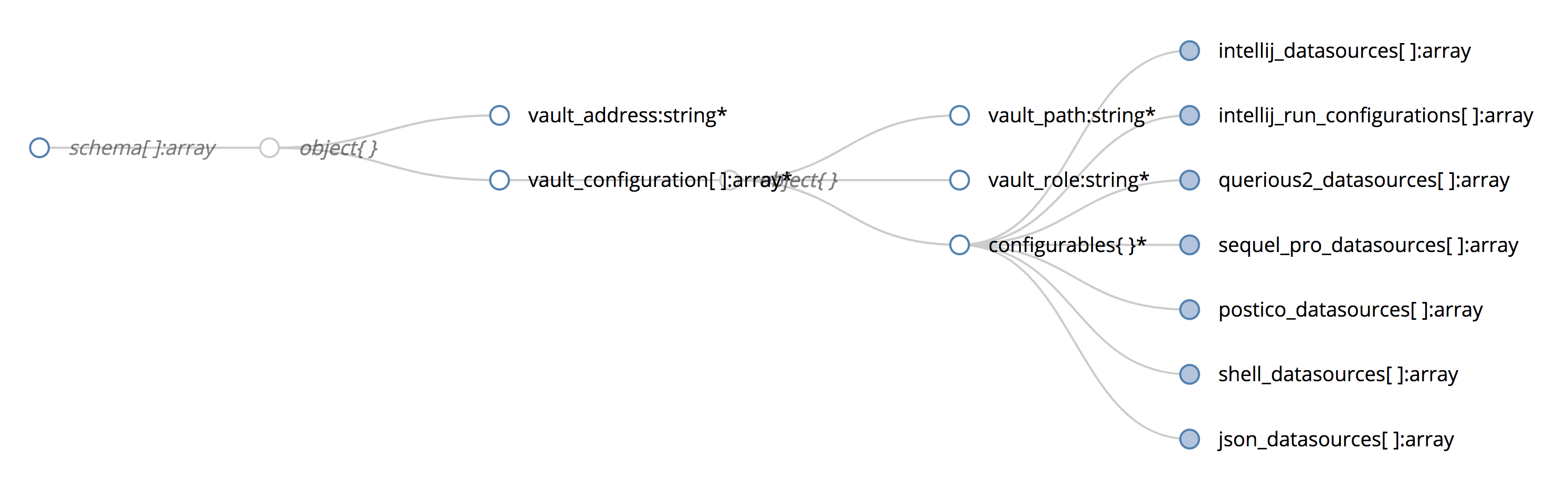
type AmanarConfiguration struct {
Constant *Constant `json:"constant,omitempty" yaml:"constant,omitempty"` // Amanar is able to render constants, which are pieces of information that do not depend on; Vault. This allows Amanar to be used to configure local static credentials in addition to; Vault-derived ones.
VaultAddress *string `json:"vault_address,omitempty" yaml:"vault_address,omitempty"` // The address to a particular vault. Vault addresses usually differ for different; environments. For example, we may have one vault address for production and another for; staging.
VaultConfiguration []VaultConfiguration `json:"vault_configuration" yaml:"vault_configuration"`
}
func (*AmanarConfiguration) MarshalYaml ¶
func (cs *AmanarConfiguration) MarshalYaml() ([]byte, error)
type Configurables ¶
type Configurables struct {
IntellijDatasources []IntellijDatasource `json:"intellij_datasources" yaml:"intellij_datasources"` // Allows IntelliJ datasource usernames and passwords to be changed. Most useful for; DataGrip and databases within IntelliJ Ultimate.
IntellijRunConfigurations []IntellijRunConfiguration `json:"intellij_run_configurations" yaml:"intellij_run_configurations"` // Allows changes to database access credentials within IntelliJ run configurations.
JSONDatasources []JSONDatasource `json:"json_datasources" yaml:"json_datasources"` // Allows a JSON file to be generated containing usernames and passwords.
PosticoDatasources []PosticoDatasource `json:"postico_datasources" yaml:"postico_datasources"` // Allows changes to database access credentials stored in a Postico SQLite database.
Querious2Datasources []Querious2Datasource `json:"querious2_datasources" yaml:"querious2_datasources"` // Allows changes to database access credentials stored in a Querious 2 SQLite database.
SequelProDatasources []SequelProDatasource `json:"sequel_pro_datasources" yaml:"sequel_pro_datasources"` // Allows changes to database access credentials for Sequel Pro plists.
ShellDatasources []ShellDatasource `json:"shell_datasources" yaml:"shell_datasources"` // Allows a file to be generated in a shell script that contains exports of environment; variables containing the new credentials.
TemplateDatasources []TemplateDatasource `json:"template_datasources" yaml:"template_datasources"` // Fills credentials into a provided Go template string or template file and prints the; result to stdout. The Credentials object is set as the dot context and its fields; (.Username and .Password) are available. Unlike the other datasources, templates are; generated anew each time and do not attempt to find previously existing keys to modify.; Go templates are documented here: https://golang.org/pkg/text/template/
}
type ConfigurationProcessor ¶
type ConfigurationProcessor interface {
ProcessConfig()
}
func NewConfigurationProcessor ¶
func NewConfigurationProcessor(githubToken string, ac AmanarConfiguration, writer io.Writer) (ConfigurationProcessor, error)
type Constant ¶
type Constant struct {
Template *string `json:"template,omitempty" yaml:"template,omitempty"` // A constant Go template string that will be rendered.
TemplatePath *string `json:"template_path,omitempty" yaml:"template_path,omitempty"` // A path to a Go template file that will be rendered.
}
Amanar is able to render constants, which are pieces of information that do not depend on Vault. This allows Amanar to be used to configure local static credentials in addition to Vault-derived ones.
func (*Constant) GetTemplate ¶
func (*Constant) GetTemplatePath ¶
type ConstantConfigurationProcessor ¶
type ConstantConfigurationProcessor struct {
// contains filtered or unexported fields
}
func (ConstantConfigurationProcessor) ProcessConfig ¶
func (c ConstantConfigurationProcessor) ProcessConfig()
type Credentials ¶
func CreateCredentialsFromSecret ¶
func CreateCredentialsFromSecret(secret *api.Secret) (*Credentials, error)
type Flower ¶
type Flower interface {
Name() string
UpdateWithCredentials(credentials *Credentials) error
PersistChanges() error
}
type GithubLoginBody ¶
type GithubLoginBody struct {
Token string `json:"token"`
}
type IntellijDatasource ¶
type IntellijDatasource struct {
DatabaseUUID string `json:"database_uuid" yaml:"database_uuid"` // The IntelliJ UUID for the database you want to update. You can find this by examining the; dataSources.local.xml file.
DatasourceFilePath string `json:"datasource_file_path" yaml:"datasource_file_path"` // The path to IntelliJ data sources file. The file is typically called; dataSources.local.xml.
}
type IntellijDatasourceFile ¶
A IntellijDatasourceFile is an XML document containing This struct and methods allows updating of the username in such a configuration. DataGrip can store usernames in its configuration and passwords in the Keyring, or it can store both a username and password in a URL-like format in its config files. This updater assumes that the former is the case.
func NewIntellijDatasourceFile ¶
func NewIntellijDatasourceFile(filepath string) (*IntellijDatasourceFile, error)
Tested with DataGrip 2017.2
func (*IntellijDatasourceFile) UpdateUsername ¶
func (dc *IntellijDatasourceFile) UpdateUsername(databaseUuid string, newUsername string) (oldUsername string, err error)
func (*IntellijDatasourceFile) WriteToFile ¶
func (dc *IntellijDatasourceFile) WriteToFile() error
type IntellijDatasourceFlow ¶
type IntellijDatasourceFlow struct {
IntellijDatasource
// contains filtered or unexported fields
}
An IntellijDatasourceFlow knows how to update the username and password for a single database with a particular IntelliJ UUID. It does this by using dataSources.local.xml files.
func NewIntellijDatasourceFlow ¶
func NewIntellijDatasourceFlow(config *IntellijDatasource) (*IntellijDatasourceFlow, error)
func (*IntellijDatasourceFlow) Name ¶
func (ds *IntellijDatasourceFlow) Name() string
func (*IntellijDatasourceFlow) PersistChanges ¶
func (ds *IntellijDatasourceFlow) PersistChanges() (err error)
func (*IntellijDatasourceFlow) UpdateWithCredentials ¶
func (ds *IntellijDatasourceFlow) UpdateWithCredentials(credentials *Credentials) (err error)
type IntellijRunConfig ¶
func NewIntellijRunConfig ¶
func NewIntellijRunConfig(filepath string) (*IntellijRunConfig, error)
func (*IntellijRunConfig) UpdateEnvironmentVariable ¶
func (rc *IntellijRunConfig) UpdateEnvironmentVariable(environmentVariable, databaseHost string, credentials *Credentials) (err error)
func (*IntellijRunConfig) WriteToFile ¶
func (rc *IntellijRunConfig) WriteToFile() (err error)
type IntellijRunConfigsFlow ¶
type IntellijRunConfigsFlow struct {
IntellijRunConfiguration
// contains filtered or unexported fields
}
func NewIntellijRunConfigsFlow ¶
func NewIntellijRunConfigsFlow(config *IntellijRunConfiguration) (*IntellijRunConfigsFlow, error)
func (*IntellijRunConfigsFlow) Name ¶
func (rc *IntellijRunConfigsFlow) Name() string
func (*IntellijRunConfigsFlow) PersistChanges ¶
func (rc *IntellijRunConfigsFlow) PersistChanges() (err error)
func (*IntellijRunConfigsFlow) UpdateWithCredentials ¶
func (rc *IntellijRunConfigsFlow) UpdateWithCredentials(credentials *Credentials) (err error)
type IntellijRunConfiguration ¶
type IntellijRunConfiguration struct {
DatabaseHost string `json:"database_host" yaml:"database_host"` // The username and password for the URL will only be updated if the host of URL in the; environment variable matches this string.
EnvironmentVariable string `json:"environment_variable" yaml:"environment_variable"` // The environment variable in the run configuration under which the database connection
RunConfigurationsFolderPath string `json:"run_configurations_folder_path" yaml:"run_configurations_folder_path"` // A directory containing all IntelliJ run configurations to be examined. Usually located in; .idea/runConfigurations. Run configurations may need to be shared before becoming visible; in this folder.
}
type JSONCredential ¶
type JSONCredentials ¶
type JSONCredentials []JSONCredential
func UnmarshalJSONCredentials ¶
func UnmarshalJSONCredentials(data []byte) (JSONCredentials, error)
func (*JSONCredentials) Marshal ¶
func (r *JSONCredentials) Marshal() ([]byte, error)
type JSONDatasource ¶
type JSONFlow ¶
type JSONFlow struct {
JSONDatasource
// contains filtered or unexported fields
}
func NewJSONFlow ¶
func NewJSONFlow(config *JSONDatasource) (*JSONFlow, error)
func (*JSONFlow) PersistChanges ¶
func (*JSONFlow) UpdateWithCredentials ¶
func (sf *JSONFlow) UpdateWithCredentials(credentials *Credentials) error
type JsonBytesSchemaValidator ¶
type JsonBytesSchemaValidator struct {
// contains filtered or unexported fields
}
func NewJsonBytesSchemaValidator ¶
func NewJsonBytesSchemaValidator(jsonBytes []byte) *JsonBytesSchemaValidator
func (JsonBytesSchemaValidator) Validate ¶
func (j JsonBytesSchemaValidator) Validate() (err error, re []gojsonschema.ResultError)
type PosticoDatasource ¶
type PosticoDatasource struct {
DatabaseUUID string `json:"database_uuid" yaml:"database_uuid"` // The unique identifier for the Postico database to update. Can be found by looking in the; SQLite database.
PosticoSqlitePath string `json:"postico_sqlite_path" yaml:"postico_sqlite_path"` // Path to the SQLite database in which Postico stores its data. The file is typically; called ConnectionFavorites.db
}
type PosticoFavorite ¶
type PosticoFavorite struct {
UUID string
User sql.NullString
Nickname sql.NullString
Host sql.NullString
Database sql.NullString
Port sql.NullInt64
}
type PosticoFlow ¶
type PosticoFlow struct {
PosticoDatasource
// contains filtered or unexported fields
}
func NewPosticoFlow ¶
func NewPosticoFlow(config *PosticoDatasource) (*PosticoFlow, error)
func (*PosticoFlow) Name ¶
func (pf *PosticoFlow) Name() string
func (*PosticoFlow) PersistChanges ¶
func (pf *PosticoFlow) PersistChanges() (err error)
func (*PosticoFlow) UpdateWithCredentials ¶
func (pf *PosticoFlow) UpdateWithCredentials(credentials *Credentials) error
type PosticoSQLiteDatabase ¶
func NewPosticoSQLiteDatabase ¶
func NewPosticoSQLiteDatabase(filepath string) (*PosticoSQLiteDatabase, error)
func (*PosticoSQLiteDatabase) GetFavoriteFromUUID ¶
func (pdb *PosticoSQLiteDatabase) GetFavoriteFromUUID(uuid string) (*PosticoFavorite, error)
func (*PosticoSQLiteDatabase) UpdateUsername ¶
func (pdb *PosticoSQLiteDatabase) UpdateUsername(databaseUuid string, username string) error
type Querious2Datasource ¶
type Querious2Datasource struct {
DatabaseUUID string `json:"database_uuid" yaml:"database_uuid"` // The unique identifier for the Querious database to update. Can be found by looking in the; SQLite database.
Querious2SqlitePath string `json:"querious2_sqlite_path" yaml:"querious2_sqlite_path"` // Path to the SQLite database in which Querious 2 stores its data. The file is typically; called Connections.sqlite.
}
type Querious2Flow ¶
type Querious2Flow struct {
Querious2Datasource
// contains filtered or unexported fields
}
func NewQuerious2Flow ¶
func NewQuerious2Flow(config *Querious2Datasource) (*Querious2Flow, error)
func (*Querious2Flow) Name ¶
func (qf *Querious2Flow) Name() string
func (*Querious2Flow) PersistChanges ¶
func (qf *Querious2Flow) PersistChanges() (err error)
func (*Querious2Flow) UpdateWithCredentials ¶
func (qf *Querious2Flow) UpdateWithCredentials(credentials *Credentials) error
type Querious2SQLiteDatabase ¶
type Querious2SQLiteDatabase struct {
Filepath string
}
func NewQuerious2SQLiteDatabase ¶
func NewQuerious2SQLiteDatabase(filepath string) (*Querious2SQLiteDatabase, error)
func (*Querious2SQLiteDatabase) UpdateUsername ¶
func (qdb *Querious2SQLiteDatabase) UpdateUsername(databaseUuid string, username string) error
type SchemaValidator ¶
type SchemaValidator interface {
Validate() (err error, re []gojsonschema.ResultError)
// contains filtered or unexported methods
}
type SequelProDatasource ¶
type SequelProDatasource struct {
DatabaseUUID string `json:"database_uuid" yaml:"database_uuid"` // The unique identifier for the Sequel Pro database to update. Can be found by looking in; the plist.
SequelProPlistPath string `json:"sequel_pro_plist_path" yaml:"sequel_pro_plist_path"` // Path to the plist in which Sequel Pro stores its data. The file is typically called; Favorites.plist
}
type SequelProFlow ¶
type SequelProFlow struct {
SequelProDatasource
// contains filtered or unexported fields
}
func NewSequelProFlow ¶
func NewSequelProFlow(config *SequelProDatasource) (spf *SequelProFlow, err error)
func (*SequelProFlow) Name ¶
func (sp *SequelProFlow) Name() string
func (*SequelProFlow) PersistChanges ¶
func (sp *SequelProFlow) PersistChanges() (err error)
func (*SequelProFlow) UpdateWithCredentials ¶
func (sp *SequelProFlow) UpdateWithCredentials(credentials *Credentials) (err error)
type SequelProPlistItem ¶
type SequelProPlistItem struct {
ColorIndex int64 `plist:"colorIndex"`
Database string `plist:"database"`
Host string `plist:"host"`
Id int64 `plist:"id"`
Name string `plist:"name"`
Port string `plist:"port"`
Socket string `plist:"socket"`
SSHHost string `plist:"sshHost"`
SSHKeyLocation string `plist:"sshKeyLocation"`
SSHKeyLocationEnabled int `plist:"sshKeyLocationEnabled"`
SSHPort string `plist:"sshPort"`
SSHUser string `plist:"sshUser"`
SSLCACertFileLocation string `plist:"sslcaCertFileLocation"`
SSLCACertFileLocationEnabled int `plist:"sslcaCertFileLocationEnabled"`
SSLCertificateFileLocation string `plist:"sslCertificateFileLocation"`
SSLCertificateFileLocationEnabled int `plist:"sslCertificateFileLocationEnabled"`
SSLKeyFileLocation string `plist:"sslKeyFileLocation"`
SSLKeyFileLocationEnabled int `plist:"sslKeyFileLocationEnabled"`
Type int `plist:"type"`
UseSSL int `plist:"useSSL"`
User string `plist:"user"`
}
type SequelProRootPlist ¶
type SequelProRootPlist struct {
FavoritesRoot struct {
IsExpanded bool `plist:"IsExpanded"`
Name string `plist:"Name"`
Children []SequelProPlistItem `plist:"Children"`
} `plist:"Favorites Root"`
}
type ShellDatasource ¶
type ShellDatasource struct {
Filepath string `json:"filepath" yaml:"filepath"` // The path the shell script should be generated to.
PasswordVariable string `json:"password_variable" yaml:"password_variable"` // The name of the environment variable that should contain the password
UsernameVariable string `json:"username_variable" yaml:"username_variable"` // The name of the environment variable that should contain the username
}
type ShellFile ¶
func NewShellFile ¶
func (*ShellFile) UpdateCredentials ¶
func (sf *ShellFile) UpdateCredentials(usernameVariable, passwordVariable string, credentials *Credentials)
func (*ShellFile) WriteToDisk ¶
type ShellFlow ¶
type ShellFlow struct {
ShellDatasource
// contains filtered or unexported fields
}
func NewShellFlow ¶
func NewShellFlow(config *ShellDatasource) (*ShellFlow, error)
func (*ShellFlow) PersistChanges ¶
func (*ShellFlow) UpdateWithCredentials ¶
func (sf *ShellFlow) UpdateWithCredentials(credentials *Credentials) error
type StructSchemaValidator ¶
type StructSchemaValidator struct {
// contains filtered or unexported fields
}
func NewStructSchemaValidator ¶
func NewStructSchemaValidator(goStruct *Amanar) *StructSchemaValidator
func (StructSchemaValidator) Validate ¶
func (s StructSchemaValidator) Validate() (err error, re []gojsonschema.ResultError)
type TemplateDatasource ¶
type TemplateDatasource struct {
Template *string `json:"template,omitempty" yaml:"template,omitempty"` // A Go template string that will be filled in with credentials.
TemplatePath *string `json:"template_path,omitempty" yaml:"template_path,omitempty"` // The path to the Go template file that will be filled in with credentials.
}
func (*TemplateDatasource) GetTemplate ¶
func (tds *TemplateDatasource) GetTemplate() *string
func (*TemplateDatasource) GetTemplatePath ¶
func (tds *TemplateDatasource) GetTemplatePath() *string
type TemplateDefiner ¶
type TemplateFlow ¶
type TemplateFlow struct {
// contains filtered or unexported fields
}
func NewTemplateFlow ¶
func NewTemplateFlow(config *TemplateDatasource, writer io.Writer) (*TemplateFlow, error)
func (*TemplateFlow) Name ¶
func (tf *TemplateFlow) Name() string
func (*TemplateFlow) PersistChanges ¶
func (tf *TemplateFlow) PersistChanges() error
func (*TemplateFlow) UpdateWithCredentials ¶
func (tf *TemplateFlow) UpdateWithCredentials(credentials *Credentials) error
type TemplateSource ¶
type TemplateSource struct {
// contains filtered or unexported fields
}
func NewTemplateSource ¶
func NewTemplateSource(definer TemplateDefiner, writer io.Writer) (source *TemplateSource, err error)
func NewTemplateSourceFromFile ¶
func NewTemplateSourceFromFile(templateFilepath *string, writer io.Writer) (*TemplateSource, error)
func NewTemplateSourceFromString ¶
func NewTemplateSourceFromString(templateString *string, writer io.Writer) (*TemplateSource, error)
func (TemplateSource) WriteToDisk ¶
func (t TemplateSource) WriteToDisk(credentials Credentials) error
func (TemplateSource) WriteToDiskWithoutContext ¶
func (t TemplateSource) WriteToDiskWithoutContext() error
type VaultConfiguration ¶
type VaultConfiguration struct {
Configurables Configurables `json:"configurables" yaml:"configurables"`
VaultPath string `json:"vault_path" yaml:"vault_path"` // The path representing the datastore in the Vault. This is equivalent to $VAULT_PATH in; the CLI command `vault read $VAULT_PATH/creds/$VAULT_ROLE`.
VaultRole string `json:"vault_role" yaml:"vault_role"` // The role representing the permissions that are sought to the Vault datastore. This is; equivalent to $VAULT_ROLE in the CLI command `vault read $VAULT_PATH/creds/$VAULT_ROLE`.
}
A list of vault roles and paths and configuration options for output to data sources within a particular vault environment.
type VaultConfigurationProcessor ¶
type VaultConfigurationProcessor struct {
// contains filtered or unexported fields
}
func (VaultConfigurationProcessor) ProcessConfig ¶
func (v VaultConfigurationProcessor) ProcessConfig()
type VaultGithubAuthClient ¶
type VaultGithubAuthClient struct {
GithubToken string
VaultAddress string
// contains filtered or unexported fields
}
func (*VaultGithubAuthClient) GetCredential ¶
func (vc *VaultGithubAuthClient) GetCredential(vaultPath, vaultRole string) (*api.Secret, error)
func (*VaultGithubAuthClient) LoginWithGithub ¶
func (vc *VaultGithubAuthClient) LoginWithGithub() error
 Source Files
¶
Source Files
¶
- amanar_configuration.go
- amanar_interfaces.go
- amanar_yaml_configuration.go
- bindata.go
- flower.go
- intellij_datasource_file.go
- intellij_datasource_flow.go
- intellij_run_config_file.go
- intellij_run_config_flow.go
- json_credentials.go
- json_flow.go
- keychain_utils.go
- keychain_utils_compat.go
- pointer_helpers.go
- postico_flow.go
- postico_sqlite_database.go
- process_amanar.go
- process_config.go
- querious2_flow.go
- querious2_sqlite_database.go
- schema_validator.go
- secret_utils.go
- sequel_pro_flow.go
- shell_file.go
- shell_flow.go
- template_flow.go
- template_source.go
- unmarshal_config.go
- vault_client.go