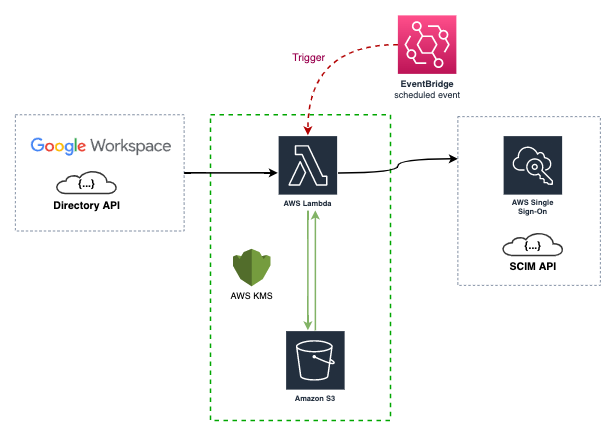
Directories
¶
Directories
¶
| Path | Synopsis |
|---|---|
|
cmd
|
|
|
idpscim
command
Package main is the entry point for the idpscim CLI application.
|
Package main is the entry point for the idpscim CLI application. |
|
idpscim/cmd
Package cmd provides the root command and configuration for the idpscim CLI application.
|
Package cmd provides the root command and configuration for the idpscim CLI application. |
|
idpscimcli
command
|
|
|
idpscimcli/cmd
Package cmd provides the root command and configuration for the idpscimcli CLI application.
|
Package cmd provides the root command and configuration for the idpscimcli CLI application. |
|
internal
|
|
|
config
Package config provides the configuration for the application.
|
Package config provides the configuration for the application. |
|
core
Package core provides core functionalities for the application.
|
Package core provides core functionalities for the application. |
|
deepcopy
Package deepcopy provides utilities for deep copying data structures.
|
Package deepcopy provides utilities for deep copying data structures. |
|
idp
Package idp provides helper functions for converting user data from an IDP to the model used in the application.
|
Package idp provides helper functions for converting user data from an IDP to the model used in the application. |
|
model
Package model provides the data structures used in the application.
|
Package model provides the data structures used in the application. |
|
repository
Package repository provides the interface for interacting with the data repository.
|
Package repository provides the interface for interacting with the data repository. |
|
scim
Package scim provides functionality to interact with SCIM APIs.
|
Package scim provides functionality to interact with SCIM APIs. |
|
setup
Package setup provides helper functions to setup the application.
|
Package setup provides helper functions to setup the application. |
|
mocks
|
|
|
aws
Package mocks is a generated GoMock package.
|
Package mocks is a generated GoMock package. |
|
core
Package mocks is a generated GoMock package.
|
Package mocks is a generated GoMock package. |
|
idp
Package mocks is a generated GoMock package.
|
Package mocks is a generated GoMock package. |
|
repository
Package mocks is a generated GoMock package.
|
Package mocks is a generated GoMock package. |
|
scim
Package mocks is a generated GoMock package.
|
Package mocks is a generated GoMock package. |
|
pkg
|
|
|
aws
Package aws provides AWS SSO SCIM API client implementation.
|
Package aws provides AWS SSO SCIM API client implementation. |
|
google
Package google provides functionality to interact with Google APIs.
|
Package google provides functionality to interact with Google APIs. |
Click to show internal directories.
Click to hide internal directories.