Documentation
¶
Documentation
¶
Index ¶
- Constants
- Variables
- func ClientInfoKey(clientID string) string
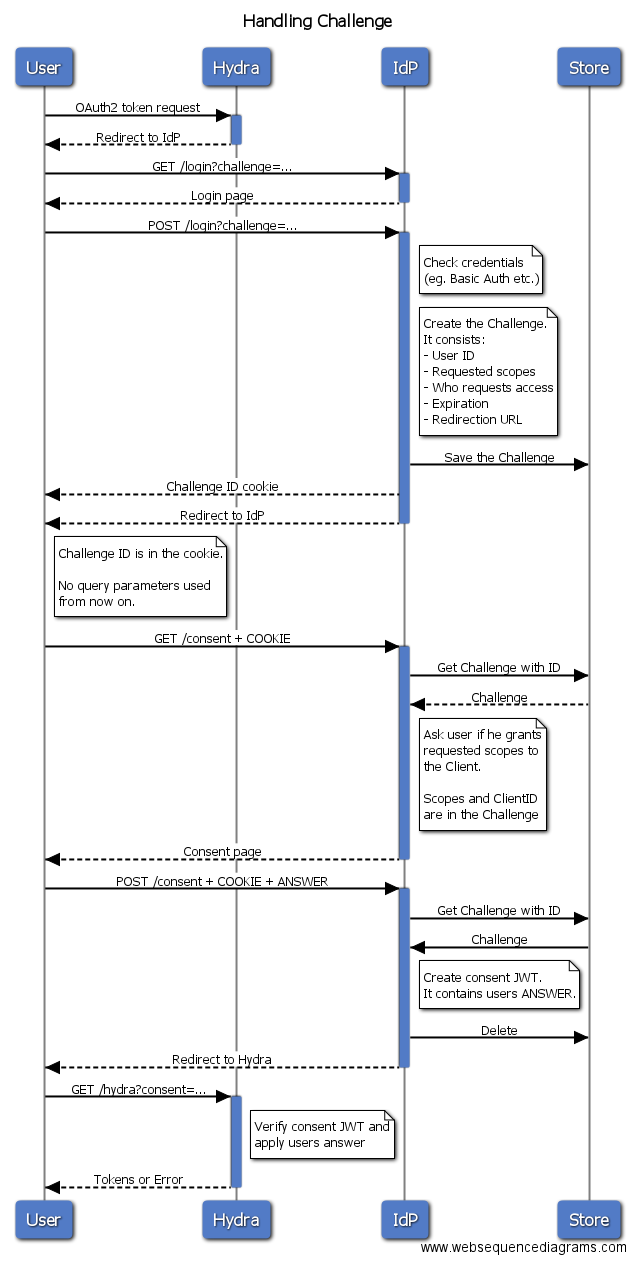
- type Challenge
- func (c *Challenge) Delete(w http.ResponseWriter, r *http.Request) error
- func (c *Challenge) GrantAccessToAll(w http.ResponseWriter, r *http.Request) error
- func (c *Challenge) RefuseAccess(w http.ResponseWriter, r *http.Request) error
- func (c *Challenge) Save(w http.ResponseWriter, r *http.Request) error
- type IDP
- func (idp *IDP) CacheConsentKey() error
- func (idp *IDP) CacheVerificationKey() error
- func (idp *IDP) Close()
- func (idp *IDP) Connect() error
- func (idp *IDP) GetChallenge(r *http.Request) (*Challenge, error)
- func (idp *IDP) GetClient(clientID string) (*hclient.Client, error)
- func (idp *IDP) GetConsentKey() (*rsa.PrivateKey, error)
- func (idp *IDP) GetVerificationKey() (*rsa.PublicKey, error)
- func (idp *IDP) NewChallenge(r *http.Request, user string) (challenge *Challenge, err error)
- type IDPConfig
Constants ¶
View Source
const ( VerifyPublicKey = "VerifyPublic" ConsentPrivateKey = "ConsentPrivate" )
View Source
const (
SessionCookieName = "challenge"
)
Variables ¶
View Source
var ( ErrorBadPublicKey = errors.New("cannot convert to public key") ErrorBadPrivateKey = errors.New("cannot convert to private key") ErrorBadRequest = errors.New("bad request") ErrorBadChallengeCookie = errors.New("bad format of the challenge cookie") ErrorChallengeExpired = errors.New("challenge expired") ErrorNoSuchClient = errors.New("there's no OIDC Client with such id") ErrorBadKey = errors.New("bad key stored in the cache ") ErrorNotInCache = errors.New("cache doesn't have the requested data") )
Functions ¶
func ClientInfoKey ¶
Types ¶
type Challenge ¶
type Challenge struct {
Client *hclient.Client
Expires time.Time
Redirect string
Scopes []string
// Set in the challenge endpoint, after authenticated.
User string
// contains filtered or unexported fields
}
func (*Challenge) GrantAccessToAll ¶
func (*Challenge) RefuseAccess ¶
type IDP ¶
type IDP struct {
// contains filtered or unexported fields
}
func (*IDP) CacheConsentKey ¶
func (*IDP) CacheVerificationKey ¶
func (*IDP) GetConsentKey ¶
func (idp *IDP) GetConsentKey() (*rsa.PrivateKey, error)
type IDPConfig ¶
type IDPConfig struct {
ClientID string `yaml:"client_id"`
ClientSecret string `yaml:"client_secret"`
ClusterURL string `yaml:"hydra_address"`
KeyCacheExpiration time.Duration `yaml:"key_cache_expiration"`
ClientCacheExpiration time.Duration `yaml:"client_cache_expiration"`
CacheCleanupInterval time.Duration `yaml:"cache_cleanup_interval"`
ChallengeStore sessions.Store
}
Click to show internal directories.
Click to hide internal directories.